Laser Fault Injection on a Budget: DEFCON 33 Showcase
Posted on Fri 15 August 2025 in Projects • Tagged with Electronics, FPGA, Exploit
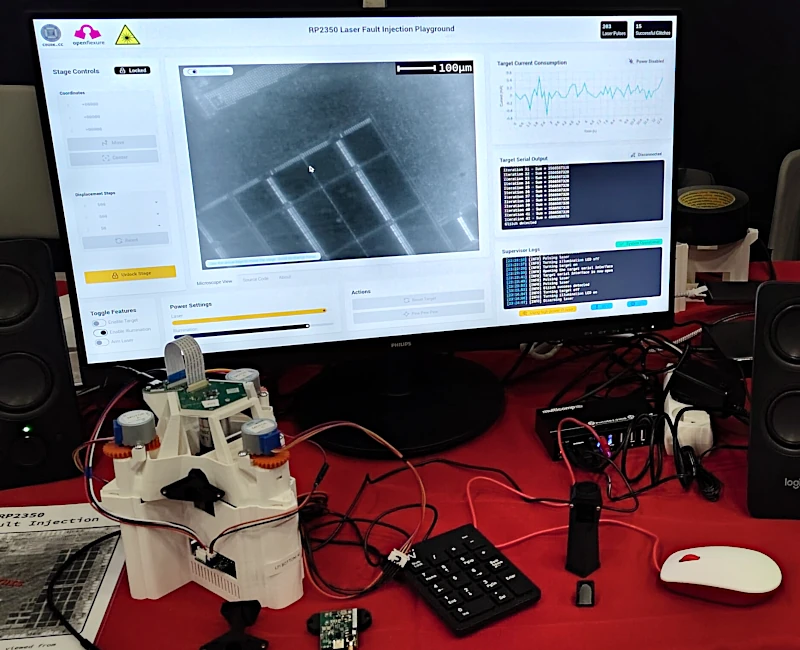
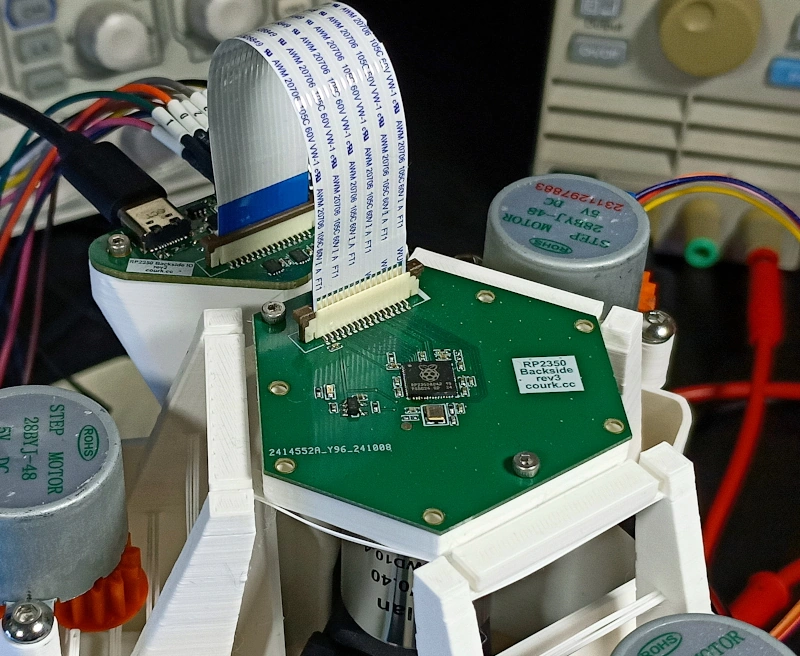
Following my work on bypassing the Secure Boot feature of the RP2350 microcontroller using laser fault injection (see the relevant article for more details), I was honored to be invited to the 33rd edition of the DEFCON convention by Raspberry Pi.
There, I showcased my budget-friendly “Laser Fault Injection Platform” and gave two small talks discussing its design.
This short article provides access to some of the materials presented at the conference, including slides, and additional source code.
Continue reading